https://xkcd.com/936/
I know that protecting data with a username/password combination is very old-fashioned and dates back to the emergence of the UNIX operating system in the 1960’s. Originally intended to distinguish users playing the game Space Travel during the night when the then-common DEC PDP-7 mainframe at Bell Labs was idle, since more than 50 years it is the only cheap, widespread and simple to use authentication tool available.
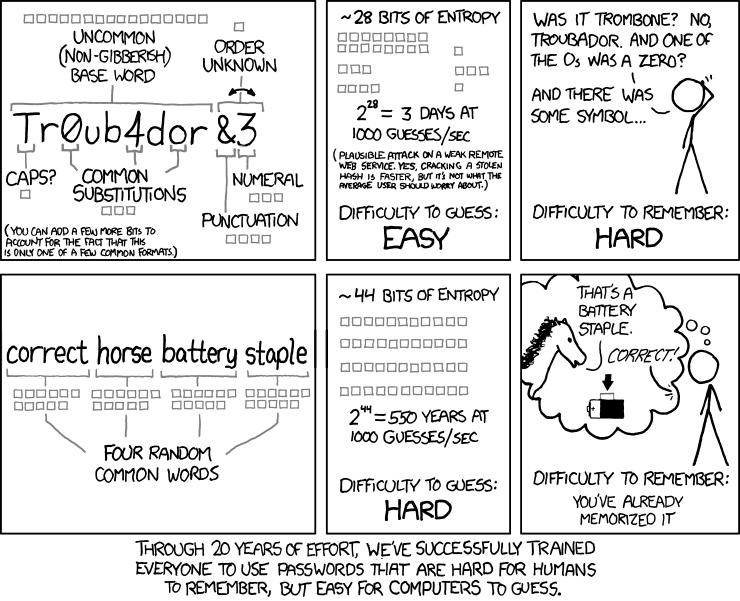
Why do I need a good password?
However the authentication and authorization procedure described on this site is one of the most important security tools the system uses to guard against unauthorized access. Knowing a password and having physical access to a terminal such as a networked Macintosh or PC are all that an unauthorized user needs to gain access to a system.
Once such a user has logged on, he or she can steal data and corrupt the system in subtle ways.
Remember, a penetrator’s actions can be traced only to your account, and you will be held accountable. It is your responsibility to ensure that your account is not compromised.
Protect your password by following these guidelines:
- Never share your password. When you tell someone your password and let them log in to your account, the system loses its ability to hold individual users accountable for their own actions.
- Do not write down your password. Many system penetrations occur simply because a user wrote his or her password on a terminal. If a password must be recorded, keep it under lock and key.
- Never use an old password again. This increases the probability that someone can guess the password. If you use the same password as the one you used, e.g., at the site you were before, a penetrator who broke into your account on one system automatically has full access to your account on the other. The passwd program doesn’t allow you to reuse old passwords.
- Never type a password while someone is watching. It is possible to steal a password simply by watching someone type it. Be especially careful if you are using a terminal in a public area, e.g., outside the institute.
Although these procedures add a small amount of effort to your access to the network system, they help to avoid system compromise.
How do I choose a good password?
If you select to choose your own password, choose your password wisely:
- Select passwords that are hard to guess. Taking the first letters of the words of a (for you) easy-to-remember sentence including unusual capitalization and punctuation for example would be a good choice.
- Never use an ordinary word or a proper name, your spouse’s, child’s, or pet’s name, your birthday, your address, or a machine name, even if these words are specified backward, permuted in some other way, or have a number added to the front or back.
- Never choose a password that contains letters only.